
REDUCE DATA ACCESS AND PERMISSIONS AND AUTOMATE CONTROLS
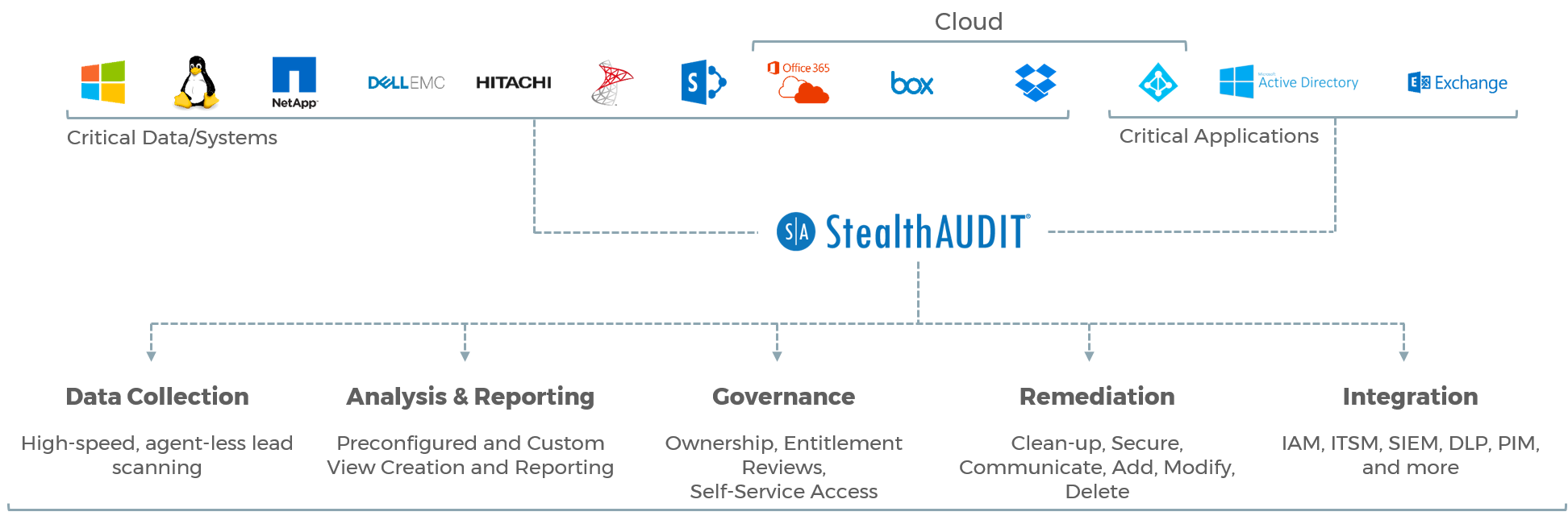
StealthAUDIT provides an automated, scalable, interoperable platform to govern unstructured data. Interoperability with IAM, HR systems, and other applications facilitates automated workflows to secure sensitive data, apply a consistent permissions model and enforce least-privileged access control.
 GOVERN ACCESSPut the business owners of information in charge of access, and align security realities with business expectations.
GOVERN ACCESSPut the business owners of information in charge of access, and align security realities with business expectations. AUTOMATE CONTROLSAutomate least privilege access for file systems to facilitate effective governance at scale and drastically accelerate time-to-value.
AUTOMATE CONTROLSAutomate least privilege access for file systems to facilitate effective governance at scale and drastically accelerate time-to-value. MONITOR ACTIVITYAnswer your most pressing security questions in real time: Who is accessing my data? What are they doing with it? Where did that folder go?
MONITOR ACTIVITYAnswer your most pressing security questions in real time: Who is accessing my data? What are they doing with it? Where did that folder go? DISCOVER & CLASSIFY SENSITIVE DATAAutomate the process of finding the business owners of data so they can make decisions data security and clean-up.
DISCOVER & CLASSIFY SENSITIVE DATAAutomate the process of finding the business owners of data so they can make decisions data security and clean-up. IDENTIFY BUSINESS OWNERSAutomate the process of finding the business owners of data so they can make decisions data security and clean-up.
IDENTIFY BUSINESS OWNERSAutomate the process of finding the business owners of data so they can make decisions data security and clean-up. REMEDIATE OPEN ACCESSEliminate one of the greatest risk to your data easily and quickly, reducing the threat surface and the effectiveness of any ransomware attack.
REMEDIATE OPEN ACCESSEliminate one of the greatest risk to your data easily and quickly, reducing the threat surface and the effectiveness of any ransomware attack.
